
A new Phobos ransomware variant frames the popular VX-Underground malware-sharing collective, indicating the group is behind attacks using the encryptor.
Phobos launched in 2018 in what is believed to be a ransomware-as-a-service derived from the Crysis ransomware family. As part of this operation, a group of threat actors manage the development of the ransomware and hold the master decryption key, while other threat actors act as affiliates to breach networks and encrypt devices.
While Phobos has been around for a long time, it never evolved into an "elite" operation known for conducting massive attacks and demanding millions of dollars.
However, that does not mean it is not a big operation, as it sees wide distribution through many affiliated threat actors and accounts for 4% of all submissions to the ID Ransomware service in 2023.
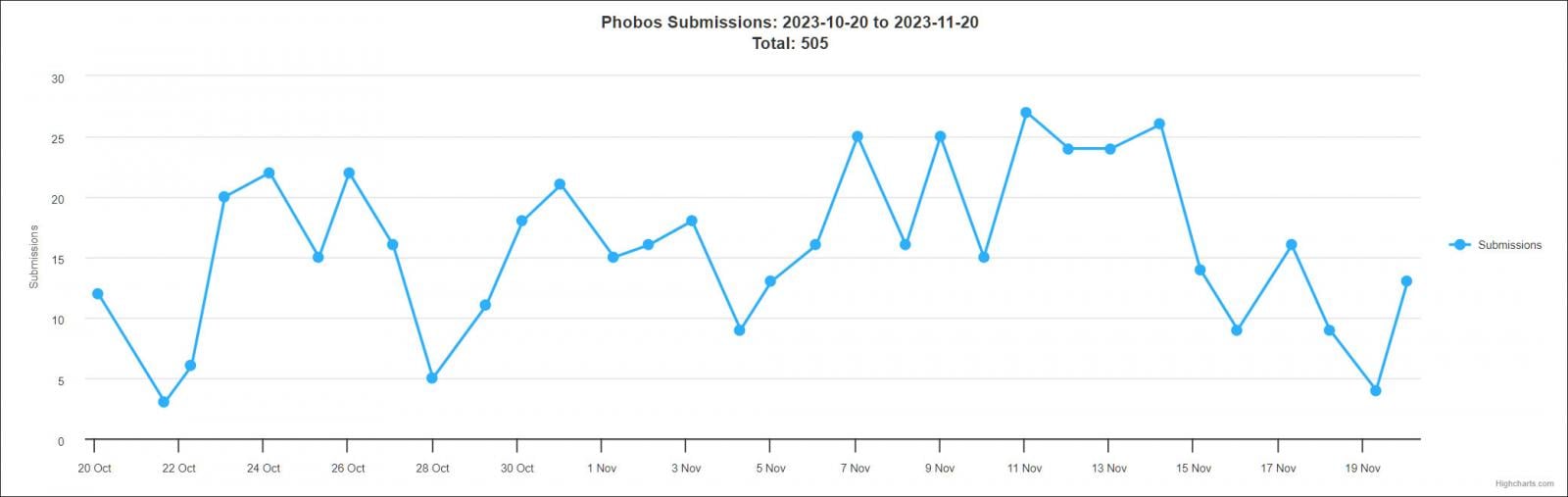
Source: ID Ransomware
Framing VX
Today, ransomware hunter PCrisk found a new variant of the Phobos ransomware that attempts to frame the VX-Underground community.
When encrypting files, the malware will append the .id[[unique_id].[staff@vx-underground.org].VXUG string, with the email being legitimate and the final extension 'VXUG,' standing for VX-Underground.
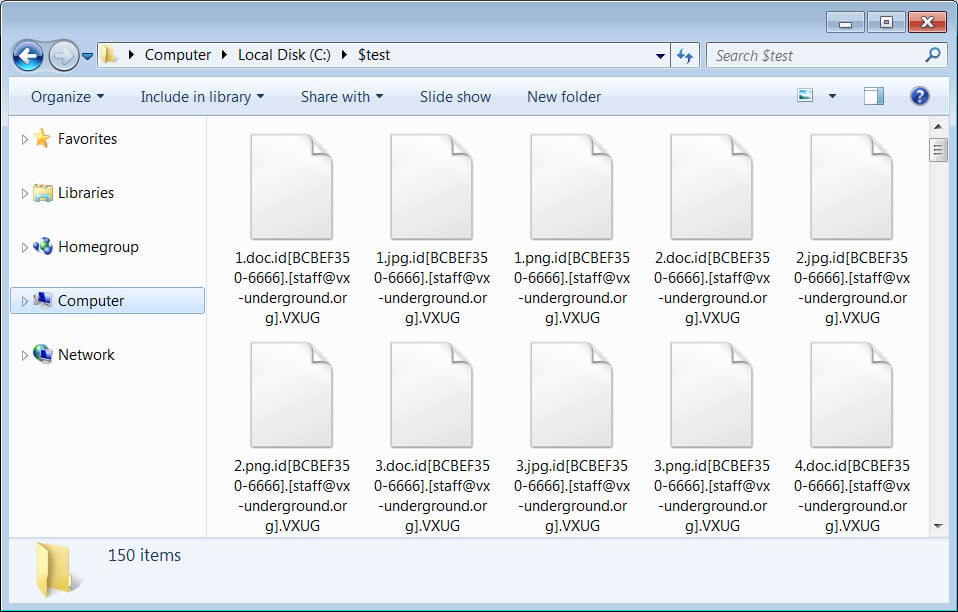
Source: BleepingComputer
When finished, Phobos will create two ransom notes on the Windows Desktop and elsewhere.
The first is a text ransom note named 'Buy Black Mass Volume II.txt,' which pokes some fun at VX by saying that the decryption password is not "infected," the password used on all VX malware archives.
"!!! All of your files are encrypted !!!
To decrypt them send e-mail to this address: staff@vx-underground.org.
If we don't answer in 48h., send message to this twitter: @vxunderground
and no the decryption password is not "infected""
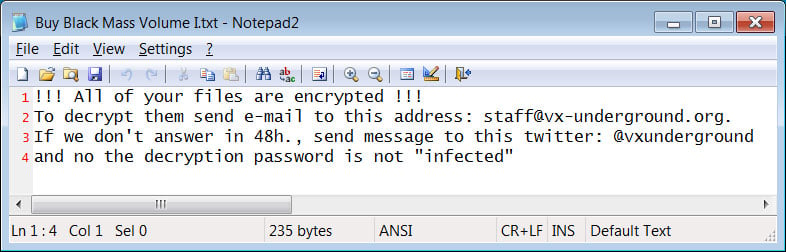
Source: BleepingComputer
The second is an HTA file named 'Buy Black Mass Volume II.hta,' your standard Phobos ransom note customized to utilize the VX-Underground logo, name, and contact info. Black Mass are books written by the VX-Underground and sold on Amazon.
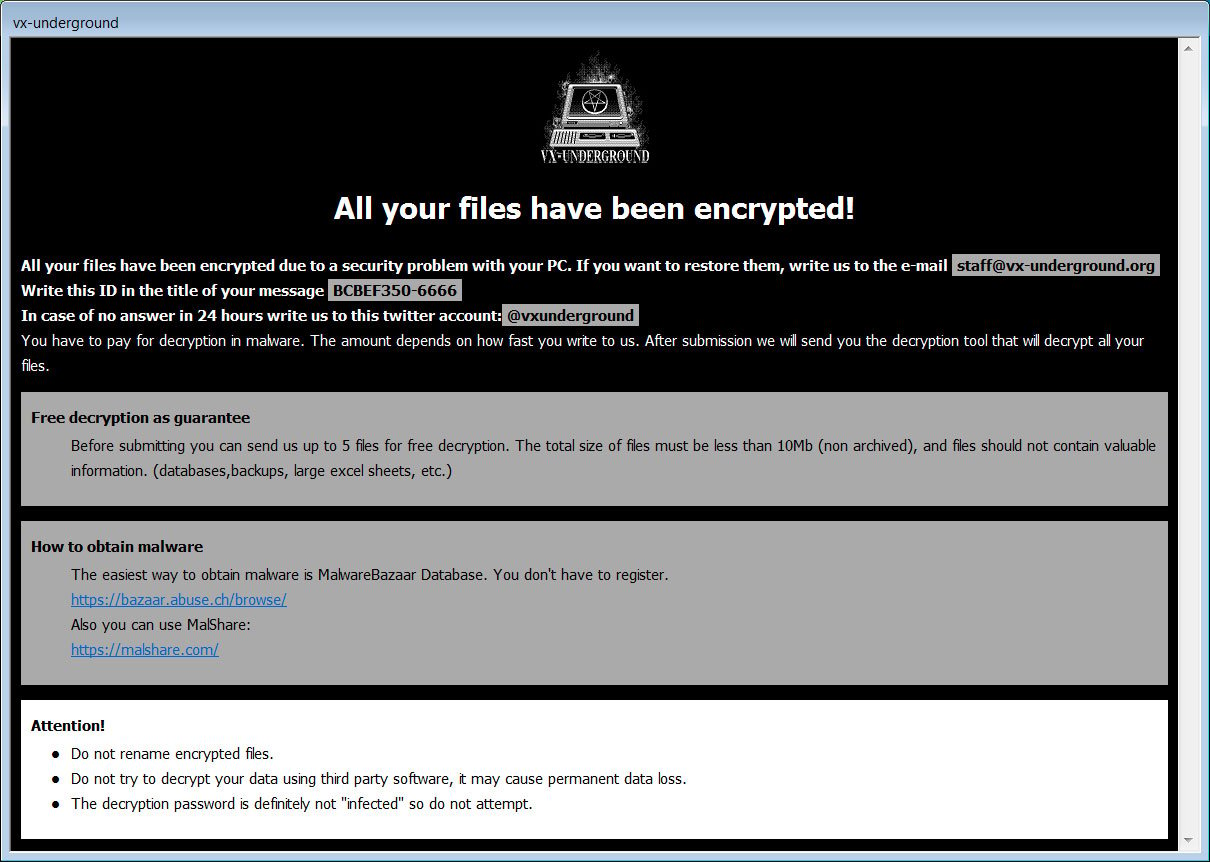
Source: BleepingComputer
Watching the watchers
Like security researchers, threat actors are involved in the online infosec and cybersecurity communities, actively participating in discussions or quietly watching from the sidelines. This monitoring, though, has led to similar taunts being added to malware and ransomware in the past.
For example, when REvil's precursor, GandCrab, was released, the threat actors named their command and control servers after BleepingComputer, Emsisoft, ESET, and NoMoreRansom.
While that was a good-natured taunting of those involved in ransomware monitoring and research, other examples took a darker turn.
In 2016, the developer of the Apocalypse ransomware began embedding abusive comments about ransomware expert Fabian Wosar in its 'Fabiansomware' encryptors out of frustration that Wosar kept finding weaknesses in the encryption.
In 2020, a developer for the Maze ransomware created a data wiper/MBR Locker named after the late security researcher Vitali Kremez and Sentinel One.
The Maze developer told BleepingComputer when they released the decryption keys that they distributed the wiper to annoy Kremez, who has been posting negative tweets about the ransomware operation.
More recently, ransomware known as 'Azov Ransomware" was heavily distributed through pirated software, key generators, and adware bundles worldwide.
This ransomware claimed to have been created by myself, BleepingComputer, Hasherazade, MalwareHunterTeam, Michael Gillespie, and Vitali Kremez, telling victims to contact us for a decryption key.
For those who interact with malware developers, you always run the risk of being included in one of their projects.
While the taunting is mostly good-natured, in some cases, like we saw with Azov and the Kremez Wiper, it can get a bit nasty.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now